Keeping Members Secure
Credential Comparisons
July 14, 2015
Professionals and companies around the world use LinkedIn to network, post and engage with others in their professional community. The role of the LinkedIn Trust & Safety team is to ensure that this positive experience for our members is not eroded by bad actors. This team puts its experience to work to make LinkedIn a safe and secure place for our members, customers, and companies to engage with each other.
One of the ways we do this is by proactively seeking out email address+password combinations that have been obtained by hackers and shared online. We do this through a number of avenues - with roughly 75% coming from vendors that scour the darknet and the remainder coming from our searches of common locations that hackers drop credentials.
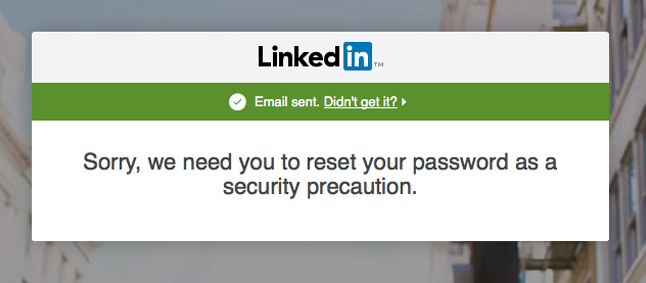
Acquired credentials that are in clear text are run through a system that standardizes the format and compares the email address to those of our members. The email addresses that match a member account have the acquired password hashed and compared to the password hash for that member’s account. If there’s a match, the system automatically invalidates the member’s password and notifies the impacted member (via email) so they can reset it. Should the member attempt to log in anyway, they’d see a message directing them to their email for a password reset.
When the team finds passwords that are hashed or encrypted, those are run through an offline system to crack the hash (if possible), and the results are then run through the same process as clear text passwords. Once we’ve run the credential through our systems, they’re purged in an effort to further protect members.
This system has been very successful in keeping members safe, and we’re finding credentials at an increased rate every year. Last year the team acquired ~100 million credentials, and in the first half of 2015 we’ve nearly doubled that number. Applying our credential comparison process to this specific 2014 batch helped protect over 2.5 million members accounts, and we’re positioned to exceed that this year.
While we’re glad that the team is able to provide this level of protection to our members, we still strongly recommend that members do not reuse passwords across websites. Additionally, enabling Two-Step Authentication will add another layer of protection, and eliminate the possibility of a stolen or non-unique password impacting their account.